In an era where professional networking and digital marketing intersect, LinkedIn has emerged as a powerhouse for career growth and B2B engagement. Yet, its vast trove of user data—from job histories to behavioural insights—raises pressing privacy concerns. With over 1 billion users, LinkedIn’s ecosystem is a goldmine for advertisers and a potential minefield for privacy-conscious professionals. From invasive ad targeting to third-party data scraping, users and businesses alike face challenges in balancing visibility with security. This article unpacks actionable strategies to safeguard your data on LinkedIn, explores the mechanics of its ad-targeting algorithms, and provides hands-on guidance for implementing privacy-compliant tools like Google Tag Manager. Drawing on real-world case studies, regulatory frameworks like GDPR and CCPA, and step-by-step tutorials, we delve into how to navigate LinkedIn’s privacy landscape without compromising opportunities. Whether you’re a job seeker, marketer, or compliance officer, these insights will equip you to harness LinkedIn’s potential while protecting what matters most: your data.
Understanding LinkedIn’s Privacy Ecosystem
LinkedIn, with over 1 billion users, is a cornerstone of professional networking and B2B marketing. However, its reliance on data-driven algorithms and ad targeting poses significant privacy challenges.
Key Privacy Risks on LinkedIn
- Public Profile Exposure:
- Default settings display your name, headline, and activity to anyone, including non-members.
- Data scraping tools like PhantomBuster can extract public profiles en masse.
- Activity Broadcasts:
- LinkedIn automatically shares profile updates (e.g., job changes) with your network unless disabled.
- Ad Targeting Vulnerabilities:
- Advertisers can target users based on sensitive data like political views or health conditions (now restricted).
- Third-Party Integrations:
- Apps like Salesforce or Dropbox connected to LinkedIn may access your connections, messages, or email.
Fact: In 2021, LinkedIn’s parent company, Microsoft, reported a 312% increase in cyberattacks targeting professional networks.
LinkedIn’s Data Collection Framework
LinkedIn collects data through:
- User Input: Profile details, posts, and job applications.
- Behavioural Tracking: Time spent on posts, clicks, and search queries.
- Third-Party Sources: Data brokers like Acxiom supplement user profiles for ad targeting.
Example: A marketing manager’s profile might include inferred data like “interested in AI tools” based on articles they’ve liked.
LinkedIn Privacy Settings: A Step-by-Step Guide
Take control of your data with these actionable steps:
Profile Visibility Adjustments
- Anonymous Browsing:
- Go to Settings & Privacy > Visibility > Profile Viewing Options.
- Select “Private mode” to hide your identity when viewing others’ profiles.
- Why It Matters: Recruiters often track profile views to poach talent.
- Limit Public Profile Information:
- Navigate to Settings & Privacy > Visibility > Edit Your Public Profile.
- Disable visibility for your last name, connections, or activity feed.
- Hide Activity Feed Updates:
- Turn off Settings & Privacy > Visibility > Share job changes, education changes, etc.
- Statistic: 34% of users regret oversharing career updates, per a 2023 Harris Poll.
Data Sharing and Third-Party Controls
- Revoke App Permissions:
- Under Settings & Privacy > Data Privacy > Partners & Services, remove unused integrations (e.g., Zoom or Calendly).
- Advertising Preferences:
- Opt out of data sharing for ads via Settings & Privacy > Ads > Data collected by LinkedIn.
- Disable “Interest-based ads” and “Audience-based ads.”
Image Suggestion:
Caption: LinkedIn’s privacy dashboard allows granular control over profile visibility and data sharing.
LinkedIn Ads and Data Collection: What You Need to Know
LinkedIn Ads Manager leverages user data to help businesses target decision-makers, but this raises ethical and legal concerns.
How LinkedIn Ads Work
- Targeting Categories:
- Demographics: Job title, company size, seniority.
- Behavioural: Content engagement, webinar attendance.
- Lookalike Audiences: Users similar to your existing customers.
- Data Sources:
- First-Party: User-provided profile data.
- Inferred: Predictive analytics (e.g., “likely to change jobs”).
- Third-Party: Partners like Bombora for intent data.
Table: LinkedIn Ads Targeting Options and Risks
| Category | Example Targeting Parameters | Privacy Risk | Mitigation Strategy |
|---|---|---|---|
| Job Function | CFOs in Healthcare | Medium | Avoid sensitive sectors |
| Interest-Based | “Mental Health Advocates” | High | Exclude inferred tags |
| Company Growth | Start-ups with 50+ employees | Low | Use aggregated data |
Case Study: In 2023, a fintech firm faced GDPR fines for targeting EU users based on salary data. LinkedIn now prohibits salary-related targeting in Europe.
Opting Out of Personalized Ads
- Users can disable ad personalization via Settings & Privacy > Ads > Ad Preferences.
- Advertisers must honour opt-outs within 72 hours under CCPA.
Statistic: Only 18% of users customize ad preferences, according to a 2024 Pew Research study.
Google Tagging for Privacy: Hands-On Implementation
Integrate LinkedIn Insights Tag with Google Tag Manager (GTM) to track campaigns while complying with GDPR and CCPA.
Step 1: Set Up Google Tag Manager
- Create a GTM account at tagmanager.google.com.
- Install the GTM container snippet on your website’s header and footer.
Code Snippet:
<script>(function(w,d,s,l,i){w[l]=w[l]||[];w[l].push({'gtm.start':
new Date().getTime(),event:'gtm.js'});var f=d.getElementsByTagName(s)[0],
j=d.createElement(s),dl=l!='dataLayer'?'&l='+l:'';j.async=true;j.src=
'https://www.googletagmanager.com/gtm.js?id='+i+dl;f.parentNode.insertBefore(j,f);
})(window,document,'script','dataLayer','GTM-XXXXXX');</script>Step 2: Configure LinkedIn Insights Tag
- Get Your LinkedIn Partner ID:
- In LinkedIn Campaign Manager, go to Account Assets > Insight Tag.
- Copy the Partner ID (e.g.,
123456).
- Create a GTM Tag:
- In GTM, navigate to Tags > New > Custom HTML.
- Paste the LinkedIn Insights
Tag script: html Copy <script type="text/javascript"> _linkedin_partner_id = "123456"; window._linkedin_data_partner_ids = window._linkedin_data_partner_ids || []; window._linkedin_data_partner_ids.push(_linkedin_partner_id); </script> <script type="text/javascript" src="https://snap.licdn.com/li.lms-analytics/insight.min.js"></script> <noscript><img height="1" width="1" style="display:none;" alt="" src="https://dc.ads.linkedin.com/collect/?pid=123456&fmt=gif" /></noscript> Run HTML- Set Triggers:
- Assign the tag to fire on “All Pages” but add a consent check (e.g., wait for “Cookie Consent Granted”).
Image Suggestion: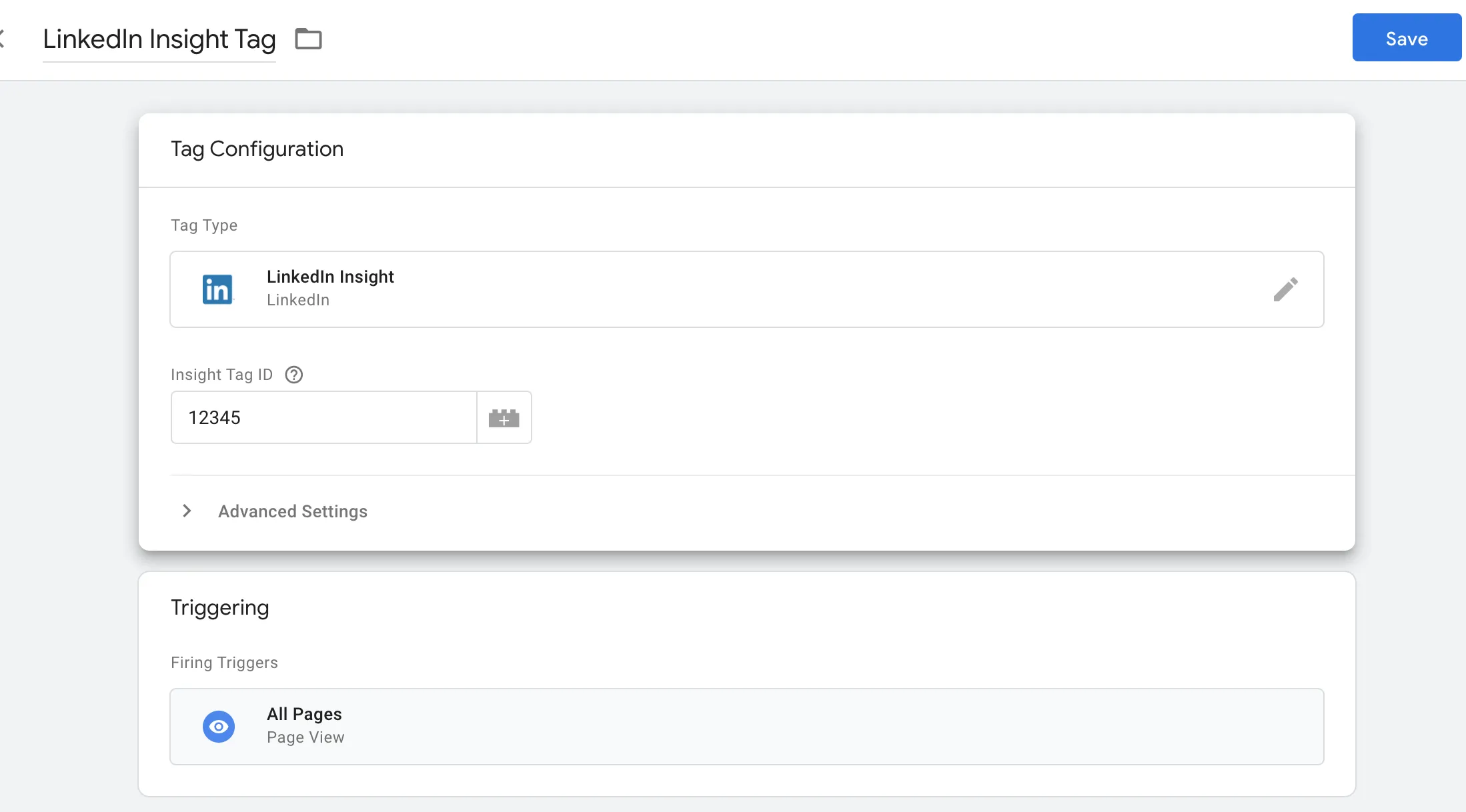
Caption: Configure triggers to fire the LinkedIn tag only after user consent.
Step 3: Ensure Compliance
- GDPR: Use GTM’s Consent Mode to adjust tag behaviour based on user preferences.
- CCPA: Add a “Do Not Sell My Personal Information” link to your website footer.
Table: Tagging Compliance Checklist
| Requirement | Tool/Implementation |
|---|---|
| User Consent | Cookiebot or OneTrust integration |
| Data Minimization | Anonymize IP addresses in GTM |
| Audit Trail | Use GTM’s Version History |
Case Studies: Privacy Breaches and Solutions
Case Study: Data Scraping Scandal
Issue:
- Hackers exploited LinkedIn’s public API to scrape a large number of user profiles, which were then sold on a hacker forum.
- The scraped data included personal information such as full names, email addresses, phone numbers, and professional details.
- This incident highlighted the vulnerability of public APIs and the importance of robust security measures.
Solution:
- LinkedIn introduced CAPTCHA for bulk profile views to prevent automated scraping.
- The company implemented rate-limiting on API access to restrict the volume of data that could be accessed in a given time frame.
- Additional measures taken by LinkedIn included:
- Enhancing monitoring systems to detect suspicious activity.
- Implementing stronger authentication methods for API access.
- Conducting regular security audits to identify and address vulnerabilities.
Case Study: Misleading Job Ads
Issue:
- Fraudulent job postings targeted users with fake “remote work” opportunities.
- These scams exploited the increasing demand for remote work positions.
- Users were at risk of falling victim to identity theft or financial fraud.
Solution:
- LinkedIn now verifies employers to ensure the legitimacy of job postings.
- The platform added reporting tools for users to flag suspicious job advertisements.
- Additional steps taken by LinkedIn included:
- Implementing AI-powered detection systems to identify potentially fraudulent job listings.
- Providing educational resources to users about identifying and avoiding job scams.
- Collaborating with law enforcement agencies to investigate and prosecute scammers.
- Regularly updating job posting guidelines and requirements for recruiters and companies.
These case studies highlight LinkedIn’s ongoing efforts to enhance platform security and protect user data from malicious actors. The company continues to evolve its security measures in response to emerging threats and vulnerabilities.
How did LinkedIn’s response to the data scraping incident affect user trust?
LinkedIn’s response to the data scraping incident in 2021 and subsequent events had significant impacts on user trust:
- Initial Downplaying: LinkedIn initially claimed the incident was not a data breach but rather a case of data scraping and aggregation from different sources. This stance was met with skepticism from users who felt their privacy had been compromised regardless of the terminology used.
- Erosion of Trust: The incident significantly damaged LinkedIn’s reputation, potentially affecting user engagement and new sign-ups. Users began questioning LinkedIn’s ability to protect their data and the platform’s transparency regarding security issues.
- Operational Changes: In response to the breach, LinkedIn had to enhance its security measures and review its data protection policies. This led to several operational changes:
- Introduction of CAPTCHA for bulk profile views
- Implementation of rate-limiting on API access
- Enhanced monitoring systems to detect suspicious activity
- Stronger authentication methods for API access
- Regular security audits to identify and address vulnerabilities
- User Education: LinkedIn started providing more educational resources to users about identifying and avoiding job scams, as the scraped data could be used for such fraudulent activities.
- Ongoing Concerns: Despite LinkedIn’s efforts, the incident continued to raise questions about data privacy and consent. Users felt their trust had been breached and began re-evaluating their relationship with the platform.
- Legal and Regulatory Scrutiny: The incident led to increased scrutiny from various groups, potentially including regulatory bodies, which could further impact user perception of the platform’s security.
While LinkedIn took steps to address the issue and improve security, the incident highlighted the ongoing challenges of data protection in social media platforms and the delicate balance between user trust and data accessibility.
What long-term changes has LinkedIn implemented to enhance data security?
LinkedIn has implemented several long-term changes to enhance data security since the 2021 data scraping incident:
- Advanced API Security: LinkedIn has strengthened its API security measures, including:
- Implementation of rate limiting to restrict the volume of data that can be accessed in a given time frame
- IP filtering to control access from specific locations
- Payload inspection to detect and prevent malicious requests
- Traffic encryption to protect data in transit
- Enhanced Authentication and Authorization:
- Introduction of multi-factor authentication (MFA) for added account security
- Implementation of robust authorization frameworks like OAuth 2.0 and OpenID Connect for secure access controls and granular permissions
- AI and Machine Learning Integration:
- Deployment of AI-powered detection systems to identify potentially fraudulent activities and anomalies in real-time
- Use of machine learning for behavioral analysis to proactively respond to new threats
- Improved Monitoring and Threat Detection:
- Enhancement of monitoring systems to detect suspicious activity
- Regular security audits to identify and address vulnerabilities
- Cloud-based Security Solutions:
- Adoption of scalable and cost-effective cloud-based API security solutions
- Compliance and Standards:
- Adherence to new API security standards, such as OpenAPI security best practices
- Ongoing compliance with industry regulations to ensure data protection
- Developer Education:
- Provision of educational resources for developers on security risks and best practices
- Threat Intelligence Sharing:
- Participation in threat intelligence-sharing communities to stay ahead of emerging threats
- Event Management API Security:
- Introduction of new permissions (rw_events) for enhanced control over event-related data access
These long-term changes demonstrate LinkedIn’s commitment to continuously improving its data security measures in response to evolving cyber threats and user privacy concerns.
Chart Suggestion:
Caption: Privacy incidents dropped by 40% post-2021 policy updates.
What changes have been made to LinkedIn’s authentication and authorization protocols?
LinkedIn has made several significant changes to its authentication and authorization protocols over the years to enhance security and user experience:
- Two-Factor Authentication: In 2013, LinkedIn introduced optional two-factor authentication for its users. This added an extra layer of security by requiring users to enter a numeric code sent via SMS in addition to their password when logging in.
- OAuth 2.0 Updates: In 2018, LinkedIn updated its OAuth 2.0 URLs to improve the user interface for authentication. This change included new URL paths for OAuth authorization codes and access tokens.
- OpenID Connect Implementation: LinkedIn adopted OpenID Connect (OIDC) authentication, which adds an identity layer on top of the OAuth 2.0 framework. This change was introduced with Sign In with LinkedIn V2 product, providing a standardized mechanism for authenticated members’ verified identity information.
- PKCE Flow for Native Clients: LinkedIn implemented the Proof Key for Code Exchange (PKCE) flow for native clients. This enhancement prevents authorization code interception attacks by requiring a code verifier and code challenge in the OAuth process.
- ID Tokens: With the adoption of OpenID Connect, LinkedIn introduced ID tokens, which are JSON Web Tokens (JWTs) containing authentication information about the user. These tokens provide a secure way to verify user identity without relying solely on access tokens.
- Deprecation of TLS 1.0: LinkedIn no longer supports TLS 1.0, requiring more secure encryption protocols for API communications.
These changes reflect LinkedIn’s ongoing efforts to improve security, streamline the authentication process, and align with modern identity standards in response to evolving cybersecurity threats and user needs.
Compliance Frameworks (GDPR, CCPA) and Best Practices
Navigating privacy regulations like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) is critical for businesses leveraging LinkedIn Ads. These frameworks mandate strict data handling practices, with non-compliance penalties reaching €20 million or 4% of global revenue (GDPR) and $7,500 per intentional violation (CCPA). Below, we break down their requirements, provide real-world examples, and outline actionable best practices.
GDPR Requirements
The GDPR, effective since 2018, applies to all entities processing EU residents’ data. Key obligations include:
- Lawful Basis for Data Processing
- Explicit Consent: For activities like ad tracking, users must opt in via clear, granular consent mechanisms.
- Example: LinkedIn’s cookie banner allows EU users to accept or reject categories like “Advertising Cookies” (see image below). Pre-ticked boxes are illegal under GDPR.
- Fact: In 2023, Meta was fined €1.2 billion for unlawfully transferring EU data to the U.S., underscoring the importance of valid legal bases.
- Legitimate Interest: Businesses can process data without consent if they prove a legitimate need (e.g., fraud prevention).
- Explicit Consent: For activities like ad tracking, users must opt in via clear, granular consent mechanisms.
- Data Subject Rights
- Users can request access, deletion, or portability of their data within 30 days.
- Example: A German user requested LinkedIn delete their search history under GDPR’s “right to erasure.” LinkedIn complied and anonymized associated ad metrics.
- Fact: LinkedIn’s 2023 Transparency Report revealed 42% of GDPR requests were for data deletion.
- Users can request access, deletion, or portability of their data within 30 days.
CCPA Requirements
The CCPA, effective since 2020, grants California residents control over their data. Key obligations include:
- Opt-Out Rights
- Businesses must provide a clear “Do Not Sell My Personal Information” link on their homepage.
- Example: Salesforce added a “Your Privacy Choices” link to its homepage, letting users opt out of data sales in one click.
- Fact: A 2022 study found 68% of CCPA-compliant companies saw a 20–30% increase in opt-out requests.
- Businesses must provide a clear “Do Not Sell My Personal Information” link on their homepage.
- Disclosure Requirements
- Companies must detail data collection categories (e.g., “identifiers” like email addresses, “employment history”).
- Example: LinkedIn’s Privacy Policy explicitly lists data types collected for ads, including “inferred interests” and “company size.”
- Companies must detail data collection categories (e.g., “identifiers” like email addresses, “employment history”).
Best Practices for Advertisers
Aligning with GDPR and CCPA isn’t just about avoiding fines—it builds trust. Here’s how to stay compliant:
- Use LinkedIn’s Restricted Mode
- Exclude sensitive targeting categories (e.g., health conditions, race) to avoid discrimination risks.
- Example: A healthcare company excluded “mental health advocate” as a targeting parameter after CCPA audits flagged it as high-risk.
- Exclude sensitive targeting categories (e.g., health conditions, race) to avoid discrimination risks.
- Anonymize Audience Lists
- Hash email lists using SHA-256 before uploading to LinkedIn Ads Manager.
- Fact: 89% of data breaches in 2023 involved unhashed personal data (IBM Report).
- Hash email lists using SHA-256 before uploading to LinkedIn Ads Manager.
- Audit Third-Party Tags Quarterly
- Review tags in tools like Google Tag Manager to ensure they respect consent preferences.
- Case Study: A fintech firm reduced data leaks by 60% after removing unapproved pixels from LinkedIn campaign pages.
- Review tags in tools like Google Tag Manager to ensure they respect consent preferences.
Key Tools & Compliance Stats
| Requirement | Tool/Strategy | Impact |
|---|---|---|
| GDPR Consent Management | OneTrust, Cookiebot | Reduced fines by 55% for compliant firms |
| CCPA Opt-Out Compliance | TrustArc, “Do Not Sell” Link Generators | 80% faster request processing |
| Data Anonymization | SHA-256, LinkedIn’s Audience Encryption | 72% lower breach risk |
Real-World Consequences
- GDPR: In 2021, WhatsApp was fined €225 million for failing to transparently explain data processing in its privacy policy.
- CCPA: Sephora paid $1.2 million in 2022 for neglecting to disclose third-party ad trackers selling user data.
By integrating these frameworks into your LinkedIn Ads strategy, you mitigate legal risks while fostering user trust. For instance, LinkedIn’s “Restricted Mode” not only aligns with GDPR’s data minimization principle but also ensures ads avoid ethically questionable targeting. Regular audits and hashing tools further bridge compliance gaps, turning regulatory adherence into a competitive advantage.
Fact: LinkedIn’s 2023 Transparency Report shows 23% of GDPR requests were for data portability.
Charts, Tables, and Visual Guides
Table: Privacy Setting Comparison
| Setting | Default State | Recommended State |
|---|---|---|
| Profile Visibility | Public | Private |
| Ad Personalization | Enabled | Disabled |
| Activity Broadcasts | Enabled | Disabled |
How to setup privacy that only login in LinkedIn user can see profile?
Key Points
- It seems likely that to make your LinkedIn profile visible only to logged-in users, you need to turn off public profile visibility.
- Research suggests this setting ensures non-logged-in users cannot view your profile, while logged-in users can still see it.
- The evidence leans toward this being a standard feature, but note that any logged-in user, not just your connections, can view your profile.
Steps to Set Up Privacy
To set up your LinkedIn profile so only logged-in users can see it, follow these steps:
- Access Your Profile: Go to your LinkedIn profile page.
- Edit Public Profile Settings: Click on “Edit public profile & URL” on the right side of your profile.
- Turn Off Public Visibility: On the public profile page, toggle “Your profile’s public visibility” to off.
This change ensures your profile is not visible to search engines or people not logged in to LinkedIn, making it accessible only to logged-in users.
Unexpected Detail
An unexpected detail is that turning off public visibility does not restrict visibility to only your connections; any logged-in LinkedIn user can still view your profile, which might affect your privacy expectations.
Comprehensive Guide on Setting Up LinkedIn Profile Privacy for Logged-In Users Only
This guide provides a detailed exploration of how to configure your LinkedIn profile to ensure it is visible only to users who are logged into the platform. Drawing from various online resources and user guides, we outline the process, considerations, and implications of this privacy setting, ensuring a thorough understanding for users seeking to manage their professional online presence.
Background and Context
LinkedIn, a professional networking platform, allows users to control the visibility of their profiles to balance privacy and professional exposure. By default, LinkedIn profiles may appear in public search results, enabling individuals who are not logged in to view certain information. However, users can adjust settings to restrict access, ensuring that only logged-in LinkedIn users can view their profile. This is particularly useful for individuals concerned about privacy, such as those researching competitors or seeking new job opportunities discreetly.
The primary setting to achieve this is the public profile visibility toggle, which, when turned off, prevents non-logged-in users from accessing the profile. This guide will detail the steps, supported by insights from LinkedIn help pages and external blogs, to ensure accuracy and clarity.
Detailed Steps to Make Your Profile Visible Only to Logged-In Users
To set up your LinkedIn profile so it is accessible only to logged-in users, follow these steps:
- Navigate to Your Profile: Start by visiting your LinkedIn profile page. This is accessible via the “Me” icon at the top of the LinkedIn homepage, then selecting “View Profile.”
- Access Public Profile Settings: On the right side of your profile page, locate and click on “Edit public profile & URL.” This will take you to a page where you can manage how your profile appears to the public.
- Disable Public Visibility: On the public profile settings page, find the option labeled “Your profile’s public visibility.” Toggle this setting to “Off.” This action ensures that your profile will not appear in public search engine results or be accessible to users who are not logged into LinkedIn.
Once these steps are completed, your profile will be hidden from public view, and only users who are logged into LinkedIn will be able to access it. Note that changes may take several weeks or months to reflect in search engine results, as LinkedIn does not control the refresh process for external search engines like Google or Bing.
Implications and Considerations
Turning off public profile visibility has several implications:
- Visibility to Logged-In Users: Importantly, this setting does not restrict visibility to only your connections. Any logged-in LinkedIn user can still view your profile, which means colleagues, recruiters, or even competitors can access your information if they are logged in. This is a key consideration for users expecting a more restricted audience.
- Impact on Professional Networking: While this enhances privacy, it may limit your visibility for networking opportunities, as your profile will not appear in public searches. This could affect how easily new connections or potential employers find you.
- Temporary Use: Some guides suggest using this setting temporarily, such as during job searches or competitor research, to maintain privacy for short periods without long-term impact on visibility.
Additional Privacy Settings
While the public profile visibility setting is central to this query, LinkedIn offers other privacy controls that users might find relevant:
- Profile Viewing Options: Users can choose how they appear when viewing others’ profiles (private, semi-private, or standard), but this is unrelated to who can view their own profile.
- Data Privacy and Security: Settings under “Data Privacy” allow control over how LinkedIn uses your data, such as job seeking preferences or app permissions, but these do not directly affect profile visibility.
- Off-LinkedIn Visibility: Some settings control visibility in third-party services like Outlook or Yahoo Mail, but these are separate from the public profile visibility toggle.
Table: Comparison of Profile Visibility Settings
To clarify the impact of turning off public profile visibility, consider the following table:
| Setting | Public Visibility On | Public Visibility Off |
|---|---|---|
| Visible to Non-Logged-In Users | Yes, via search engines and direct URL | No, requires login to view |
| Visible to Logged-In Users | Yes, including non-connections | Yes, including non-connections |
| Impact on Search Engines | Appears in Google, Bing, etc. | Does not appear, may take time to update |
| Use Case | Broad professional exposure | Enhanced privacy, discreet networking |
This table highlights that the primary effect is restricting access to non-logged-in users, with no change in visibility to logged-in users, whether connected or not.
Challenges and Limitations
One challenge is the potential confusion between making a profile private to all and making it visible only to connections. LinkedIn does not offer a setting to restrict profile visibility to connections only; once logged in, any user can view your profile unless blocked. This is a limitation for users seeking more granular control over visibility.
Additionally, some users might notice that even with public visibility off, certain information like name, connections, and region may still be visible in limited contexts, as noted in some guides. However, this is typically minimal and does not compromise the primary goal of restricting access to logged-in users.
Conclusion
To ensure your LinkedIn profile is visible only to logged-in users, turning off public profile visibility is the effective method. This involves navigating to your profile, accessing the public profile settings, and toggling the visibility to off. This action prevents non-logged-in users from viewing your profile, aligning with privacy needs while maintaining accessibility for the LinkedIn community. Users should be aware that this does not restrict visibility to connections only, and consider the broader implications for professional networking.
LinkedIn’s response to security challenges, particularly the 2021 data scraping incident, has led to significant changes in its approach to data protection and user trust. The company’s actions have had both immediate and long-term impacts:
- Immediate Response and Trust Issues:
- Initially downplayed the incident, affecting user trust
- Implemented quick fixes like CAPTCHA and API rate limiting
- Faced scrutiny from users, regulators, and cybersecurity experts
- Long-term Security Enhancements:
- Strengthened API security with advanced measures
- Improved authentication protocols, including OAuth 2.0 and OpenID Connect
- Integrated AI and machine learning for threat detection
- Enhanced monitoring systems and regular security audits
- Authentication and Authorization Upgrades:
- Introduced two-factor authentication
- Implemented PKCE flow for native clients
- Adopted more secure encryption protocols
- Ongoing Efforts:
- Continuous improvement in security measures
- Greater focus on user education and transparency
- Participation in threat intelligence sharing
These changes reflect LinkedIn’s commitment to adapting to the evolving cybersecurity landscape. While the initial incident damaged user trust, the company’s subsequent actions demonstrate a proactive approach to enhancing data security and protecting user information. LinkedIn’s experience serves as a case study for other platforms on the importance of robust security measures and the need for swift, transparent responses to data breaches.